How do you benefit from using MikroTik Network Solutions? Mini Guide.
Companies resort to developing and modernizing network systems and finding new network solutions that suit their goals and follow the approach of the tremendous development that is taking place in the field of network engineering. Mikrotik network solutions have provided capabilities that exceed the demands of companies and institutions working in the field of technology and industry.
If you are the owner of an organization or interested in the field of network engineering and are looking for practical and highly effective solutions that ensure the smooth flow of work within the network with a simplified and fast preparation with factors and ingredients such as the firewall network, VPN and hotspot.
Characteristics of Mikrotik solutions for networks within the work environment
Mikrotik provides smart network solutions in its RouterOS system including configuration, firewall, routing, MPLS, VPN, wireless, DHCP, hotspot, Quality of Service, proxy, and various tools.
Within your business environment, it will require you to check and check network security and connect the network to each other in a safe and effective way. Not only that, but it requires the establishment of an interconnection between the devices and systems operating within the work environment.
One of the most important features of the Mikrotik system in Mikrotik routers is the VPN feature.
A VPN is a virtual private network (VPN) is a method for the extension of a private network across a public network, such as the Internet. It enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network.

A VPN is created by establishing a virtual point-to-point connection through the use of dedicated connections, virtual tunneling protocols, or traffic encryption.
• Router does not have static IP.
• PPTP is not working, and not very secure even if it is.
• SSTP is not compatible with Mac OS, Android, or Windows XP.
• IPSEC is complicated to set up.
Here comes the role of the Mikrotik router in providing solutions as follows:
• Dynamic Domain Name Service (DDNS) can solve the issue of the absence of static IP.
• Third-party DDNS services often require scripts.
• Most third-party DDNS require fees.
One of the most important features of Mikrotik network solutions, which is indispensable here, whether in the work environment of companies and institutions or even inside homes for personal use, is the feature of the firewall.
MikroTik RouterOS Firewall stands between the company’s network and a public network, effectively shielding your computers from malicious hacker activity, and controlling the flow of data to the router, through the router, and from the router.
MikroTik RouterOS firewall supports filtering and security functions that form your Internet using policy.
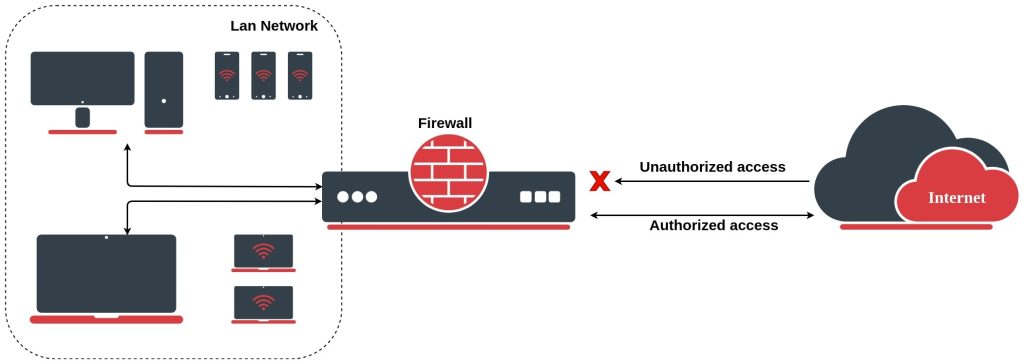
MikroTik RouterOS Firewall is very easy to manage! The system’s architecture allows easy configuration of network address translation (NAT), transparent proxies, and redirection. The Firewall filtering rules are grouped together in chains. It is very advantageous if packets can be matched against one common criterion in one chain and then passed over for processing against some other common criteria to another chain. That makes the system a whole lot easier to administrate, using a smaller number of rules to create much more precise firewalling.
Protection of the Router from unauthorized access
You can monitor connections to the addresses assigned to the router itself and allow access only from certain hosts to certain TCP ports of the router.
The Firewall controls all Internet information and warns and blocks the intrusion attempt based on rules, customized by the user.
Protection of the customer’s hosts
You can monitor connections to the addresses assigned to the customer’s network and allow access only to certain hosts and services. You endow your customers with effective and proactive defense against malicious attacks.
Using Masquerading to hide the private network behind one external address
All connections from the private addresses can be masqueraded, and that appear as coming from one external address – that of the router. The firewall will act as a gateway for your entire network to enable the office’s network to share a single, safe connection to the Internet.
Enforcing the Internet Usage Policy from the Customer’s Network
The Firewall allows you to control connections from the Customer’s Network and provides detailed traffic statistics of all the links.
Prioritizing traffic
You can mark packets by priority to ensure the fastest connection to more important packets. This guarantees that all groups always get the appropriate bandwidth, providing a controllable flow of network traffic and preventing bandwidth starvation.
Applying queuing to the outgoing packets
This feature allows limiting connection speed to a certain group of packets. The hierarchy of class enables you to build a flexible, and very logical representation of your traffic.
The need of companies and institutions for VPN and Firewall networks is one of the pillars of building the work environment to assemble and connect the networks of different places under one management and configuration, and this is what Mikrotik devices do.
As an Official Distributor of MikroTik in Egypt, Technopedia Help and Guide companies benefit from using MikroTik Routers in their networks.

